Theoretical Paper
- Computer Organization
- Data Structure
- Digital Electronics
- Object Oriented Programming
- Discrete Mathematics
- Graph Theory
- Operating Systems
- Software Engineering
- Computer Graphics
- Database Management System
- Operation Research
- Computer Networking
- Image Processing
- Internet Technologies
- Micro Processor
- E-Commerce & ERP
Practical Paper
Industrial Training
How A TSR Works
Most DOS based programs interact with memory in a very simple way: DOS loads them in memory just above itself, the programs use all the available memory they want, and then when their execution is over, the memory occupied by these programs is freed.
A TSR is different. It also gets loaded on top of DOS, but it does not go away from memory when it terminates. Instead, it remains resident in memory in a dormant state, doing nothing but occupying memory. When the TSR is in memory, other DOS programs run as usual, except that the memory occupied by the TSR is unavailable to them.
If you load more than one TSRs, each one gets loaded on the top of the previous one in a sort of TSR stack. When you hit the appropriate hot keys to bring up a TSR, you are just activating a program that is already in memory. But how on earth does the TSR get activated on hitting appropriate hot keys ? By using a trick that involves the interrupt and the IVT. As we know when an interrupt occurs the system has to find out the routine that should handle this interrupt. The system multiplies the interrupt number by 4 and uses the result to pick up the address of the routine from the IVT. This address is typically the address of the routine (ISR)which knows how to handle the interrupt.
A TSR puts itself in the middle of this process. In effect, a TSR steals the normal keyboard interrupt by replacing the address in IVT with the address of one of the TSR's routines. This routine checks each key sequence to see if it is the TSR's hot key sequence. If so, it activates the TSR. If not, it passes the control to the original ISR. You as a user would never know the difference. The only cost is a tiny bit of system time spent to execute the TSR's keyboard interrupt routine.
You can imagine that the situation would become more complicated when more than one TSR is resident in memory since each must have stolen the keyboard interrupt. When this happens, the TSR which has been loaded last gets each keystroke first. It either executes, or it passes the control to the TSR which was loaded before it. This process repeats until one of the TSRs finds its hot keys. If the keystroke doesn't match with hot keys of any of the TSRs then the control is passed to the normal BIOS routine. The essence of this entire process is caught in Figure 1.
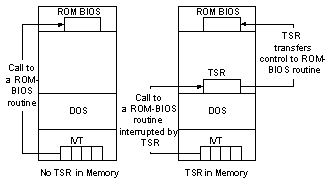
The figure explains how one TSR has hooked a single interrupt. Actual TSRs often hook many interrupts, and you may have several TSRs loaded in memory at once. That situation is much too complex. To be able to pass control to the TSRs that we propose to write, we must know a mechanism by way of which we would be able to transfer control to a routine by merely knowing the address of the routine.

