Theoretical Paper
- Computer Organization
- Data Structure
- Digital Electronics
- Object Oriented Programming
- Discrete Mathematics
- Graph Theory
- Operating Systems
- Software Engineering
- Computer Graphics
- Database Management System
- Operation Research
- Computer Networking
- Image Processing
- Internet Technologies
- Micro Processor
- E-Commerce & ERP
Practical Paper
Industrial Training
Servers and Clients
TCP/IP Services and Client/Server Operation
TCP/IP is most often studied in terms of its layer-based architecture and the protocols that it provides at those different layers. And we're certainly going to do that, don't worry. These protocols, however, represent the technical details of how TCP/IP works. They are of interest to us as students of technology, but are normally hidden from users who do not need to see the “guts” of how TCP/IP works to know that it works. Before proceeding to these details, I think it might be instructive to take a “bigger picture” look at what TCP/IP does.
TCP/IP Services
In the section describing the OSI Reference Model I mentioned that the theoretical operation of the model is based on the concept of one layer providing services to the layers above it. TCP/IP covers many layers of the OSI model, and so it collectively provides services of this sort as well in many ways. Conceptually, we can divide TCP/IP services into two groups: services provided to other protocols and services provided to end users directly.
Services Provided to Other Protocols
The first group of services consists of the core functions implemented by the main TCP/IP protocols such as IP, TCP and UDP. These services are designed to actually accomplish the internetworking functions of the protocol suite. For example, at the network layer, IP provides functions such as addressing, delivery, and datagram packaging, fragmentation and reassembly. At the transport layer, TCP and UDP are concerned with encapsulating user data and managing connections between devices. Other protocols provide routing and management functionality. Higher-layer protocols use these services, allowing them to concentrate on what they are intended to accomplish.
End-User Services
The other general types of service provided by TCP/IP are end-user services. These facilitate the operation of the applications that users run to make use of the power of the Internet and other TCP/IP networks. For example, the World Wide Web (WWW) is arguably the most important Internet application. WWW services are provided through the Hypertext Transfer Protocol (HTTP), a TCP/IP application layer protocol. HTTP in turn uses services provided by lower-level protocols. All of these details are of course hidden from the end users, which is entirely on purpose!
TCP/IP Architecture and the TCP/IP Model
The OSI reference model consists of seven layers that represent a functional division of the tasks required to implement a network. It is a conceptual tool that I often use to show how various protocols and technologies fit together to implement networks. However, it's not the only networking model that attempts to divide tasks into layers and components. The TCP/IP protocol suite was in fact created before the OSI Reference Model; as such, its inventors didn't use the OSI model to explain TCP/IP architecture (even though the OSI model is often used in TCP/IP discussions today, as you will see in this Guide, believe me.)
The TCP/IP Model
The developers of the TCP/IP protocol suite created their own architectural model to help describe its components and functions. This model goes by different names, including the TCP/IP model, the DARPA model (after the agency that was largely responsible for developing TCP/IP) and the DOD model (after the United States Department of Defense, the “D” in “DARPA”). I just call it the TCP/IP model since this seems the simplest designation for modern times.
Regardless of the model you use to represent the function of a network—and regardless of what you call that model!—the functions that the model represents are pretty much the same. This means that the TCP/IP and the OSI models are really quite similar in nature even if they don't carve up the network functionality pie in precisely the same way. There is a fairly natural correspondence between the TCP/IP and OSI layers, it just isn't always a “one-to-one” relationship. Since the OSI model is used so widely, it is common to explain the TCP/IP architecture both in terms of the TCP/IP layers and the corresponding OSI layers, and that's what I will now do.
| Port number | Protocol that uses it |
|---|---|
| 21 | File Transfer Protocol (FTP) |
| 25 | Simple Mail Transfer Protocol (SMTP) |
| 80 & 8080 | HyperText Transfer Protocol (HTTP) |
| 110 | Post Office Protocol v3 (POP3) |
| 143 | Internet Message Access Protocol (IMAP) |
| 443 | HyperText Transfer Protocol over SSL/TLS (HTTPS) |
| 666 | Doom Multiplayer game |
| 989 | Secure FTP (SFTP) |
| 23 | Telnet |
| 25565 | Minecraft Multiplayer Default Port |
| 27015 | Source Engine Multiplayer Default Port |
Several of the protocols used to transmit data across networks (including the internet) are not secure. This means that if you are one of the routers that is used to get data from one host to another, you can read the data being sent, this technique is called packet sniffing. Normally this isn't a problem as the data being transmitted isn't secret but reading other people's packets without their permission is a crime in the UK.
FTP
File Transfer Protocol (FTP) is a standard network protocol used to copy a file from one host to another over a TCP/IP-based network, such as the Internet. FTP is built on a client-server architecture. FTP users may authenticate themselves using a clear-text (unencrypted) sign-in protocol but can connect anonymously if the server is configured to allow it. FTP works on port 21.
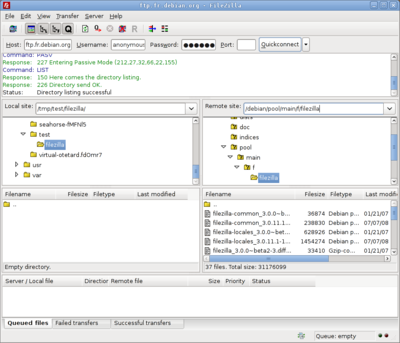
The first FTP client applications were interactive command-line tools, implementing standard commands and syntax. Graphical user interface clients have since been developed for many of the popular desktop operating systems in use today.
HTTP
The Hypertext Transfer Protocol (HTTP) is a networking protocol behind the World Wide Web. HTTP allows for transmission of Hypertext documents and webpages. HTTP works on ports 80 and 8080.
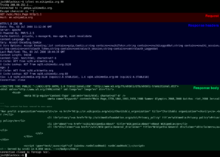
Telnet
Telnet is a network protocol used on the Internet or a local area network to provide text-oriented communications between a server and remote clients. A client will connect to the server using a terminal (black and white command line console) and can then deliver commands to the server to perform things like remote software installation or system updates. Telnet works on several different ports.

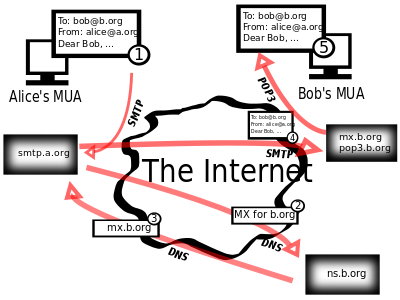
POP3, SMTP
Simple Mail Transfer Protocol (SMTP) is an Internet standard for sending electronic mail (e-mail) across Internet Protocol (IP) networks. SMTP is specified for outgoing mail transport and uses TCP port 25. The protocol for receiving mail is called the Post Office Protocol 3 and it uses port 110.
Secure protocols
Sometimes we need to send data securely over networks. There are several protocols that allow you to do this. You can normally tell if a protocol is secure if it has the letter 'S' in its name. Examples include SSH, SFTP and HTTPS (SMTP is NOT secure!)
HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is a combination of the Hypertext Transfer Protocol with the SSL/TLS protocol to provide encrypted communication and secure identification with a network web server.
HTTPS is often used when sensitive information is being sent over the internet, for example on internet banking webpages.

